HEXTAGON

Expending perimeter. Centralized control. Hextagon.
#Internet of Things
#Artificial Intelligence
#Computers
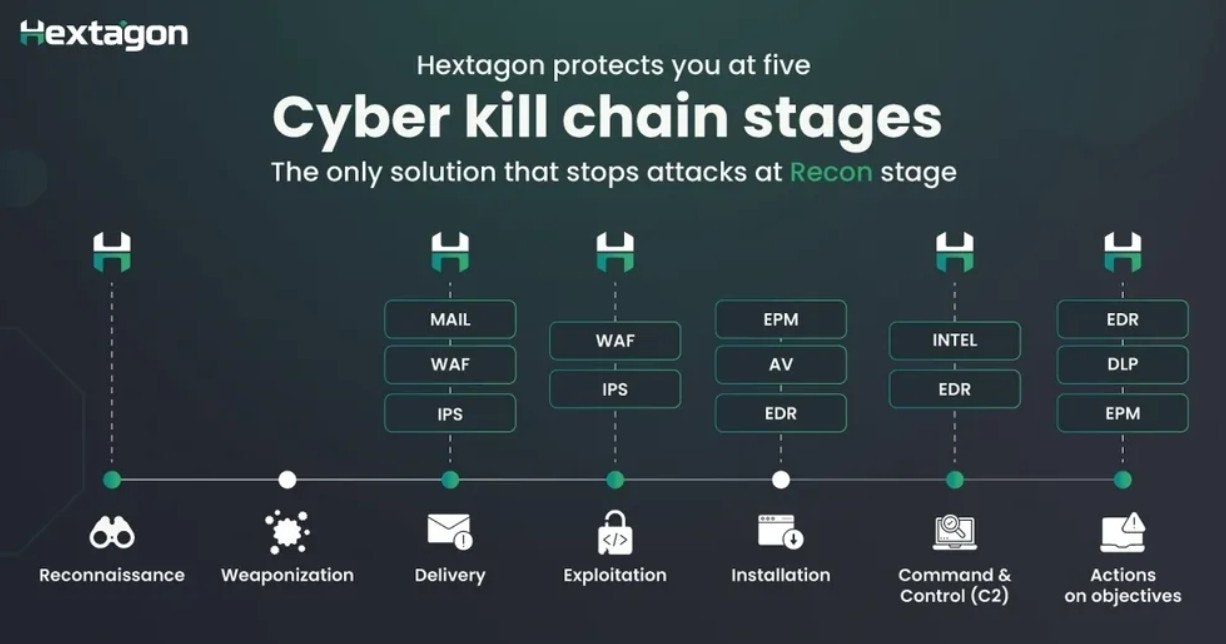
HEXTAGON – Real-time adversary behavior detection and threat disruption
Summary: HEXTAGON detects adversary behavior in real time and disrupts threats early in the attack chain by unifying threat data across On-Prem, Cloud, OT, and IoT environments to prevent breaches.
What it does
It monitors and identifies attacker activities during reconnaissance and initial access stages, then coordinates threat response across the entire security stack to stop attacks before escalation.
Who it's for
Security teams seeking proactive detection and prevention of breaches across diverse IT and operational environments.
Why it matters
It addresses the gap in early-stage attack detection, enabling intervention before breaches occur rather than reacting afterward.
